Picture this: You’re the IT head of a thriving organization. You’ve implemented firewalls, set up secure networks, and established solid security protocols. However, a lingering question remains in your mind: “Is our digital fortress impregnable?” In the rapidly evolving cybersecurity landscape, complacency can be your biggest enemy. With cyber threats becoming more sophisticated daily, relying solely on traditional security measures is akin to leaving your fortress unguarded.
The solution? A cutting-edge risk assessment tool. Integrating such a tool into your cybersecurity strategy can provide your organization with the much-needed security shield, empowering you to ward off threats before they materialize. Let’s break down the how and why of it.
Fathom the Unfathomable: What is a Risk Assessment Tool?
At its core, a cybersecurity risk assessment tool is your ally in identifying, analyzing, and evaluating potential vulnerabilities within your IT ecosystem. It scrutinizes your security systems from the perspective of a potential attacker, providing you with a bird’s-eye view of your security posture. It’s like having a dedicated security strategist, predicting risks, and devising preventive measures.
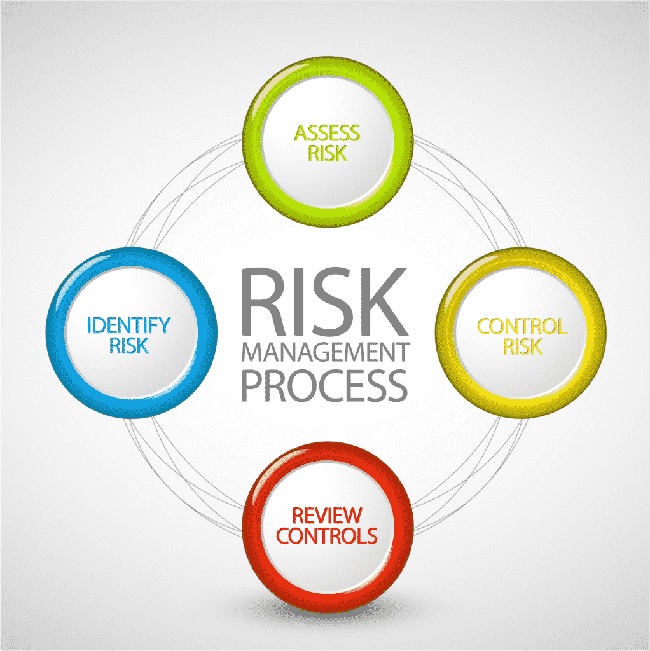
Conquer Cyber Threats: The Four-Step Process
Risk assessment tools generally follow a four-step process that gives a holistic view of your organization’s risk landscape.
- Identify Threats and Vulnerabilities: The tool scans your system to identify possible weaknesses that could be exploited. It keeps an eye out for any outdated software, insecure network connections, or other system vulnerabilities.
- Determine the Impact: It estimates the potential impact of each identified risk on your organization’s operations. Doing so gives you a clearer understanding of what’s at stake.
- Evaluate Risk Levels: The tool then assigns a risk level to each vulnerability based on the potential impact and the likelihood of the threat materializing. This step is crucial in prioritizing your defense strategy.
- Develop Mitigation Strategies: Based on the risk levels, the tool recommends mitigation strategies to eliminate or manage the identified risks. This process enables you to secure your systems rather than proactively tackle breaches.
The Future of Cybersecurity
Risk assessment tools aren’t just about defending against threats; they’re about shifting the power dynamics in your favor. They transform your cybersecurity strategy from a game of catch-up with hackers to a proactive, strategic, and robust defense mechanism.
While the technology behind these tools is continually evolving, their essence lies in their ability to provide a dynamic and holistic security solution. As a result, they empower you to stay one step ahead of potential threats, bolstering your cybersecurity strategy with actionable insights.
Maximize Your Cybersecurity Strategy
A cutting-edge risk assessment tool offers more than just threat analysis. It presents an opportunity to weave a culture of security awareness within your organization. When everyone knows potential risks and the best practices to mitigate them, cybersecurity becomes an organization-wide responsibility rather than just an IT department’s concern.
A risk assessment tool does more than just ‘assess.’ It empowers, it strategizes, and it strengthens. It takes your cybersecurity strategy from reactive to proactive, arming you with the knowledge and tools necessary to counter evolving threats.
So, are you ready to elevate your cybersecurity strategy? The time is now. After all, the key to a robust cybersecurity strategy isn’t just about warding off threats — it’s about anticipating them.